7.1.3. Lima Charlie-based Collections¶
You can deploy the Cyber Triage Collector tool with Lima Charlie. This allows you to use existing agents to collect additional data when you want to investigate an endpoint further.
Cyber Triage uses automated analysis to score artifacts as Bad or Suspicious and provides a UI to allow you to quickly investigate hosts for intrusions.
7.1.3.1. Lima Charlie Basics¶
Here are some key Lima Charlie Concepts to make sure we are using consistent terminology.
Agent-side:
Sensors are agents deployed to endpoints
Payloads extend the functionality of the sensors/agents
Server-side:
Adapters import data into Lima Charlie
Artifacts parse imported data
Extensions call into external web hooks
We are going to rely on Payloads to extend the agent functionality with the Cyber Triage Collector.
7.1.3.2. Configure Lima Charlie for Collections¶
There are two main steps to deploy the Collector using Lima Charlie:
Download and configure the Deployer Powershell script.
Add the Deployer script to Lima Charlie as a Payload
7.1.3.2.1. Download and Configure Cyber Triage Deployer Script¶
You will use the Cyber Triage Deployer script with your Lima Charlie integration. This is the same Powershell script that is used with many EDRs.
You will need to download the script and may need to make some changes based on your use case.
Some special notes about Lima Charlie we have observed:
You can’t store the configuration files inside the Lima Charlie server. So, focus on using command line arguments intead of configuration files (for S3, etc.).
Refer to Configure the Collector Deployer Powershell Script for getting and configuring the script.
You’ll add it to the Lima Charlie server as a Payload
7.1.3.2.2. Add the Script as a Payload¶
After you’ve locally configured and tested the Deployer script, you can add it to the server.
Choose the Payload option from the left menu.
Choose the Add Payload button
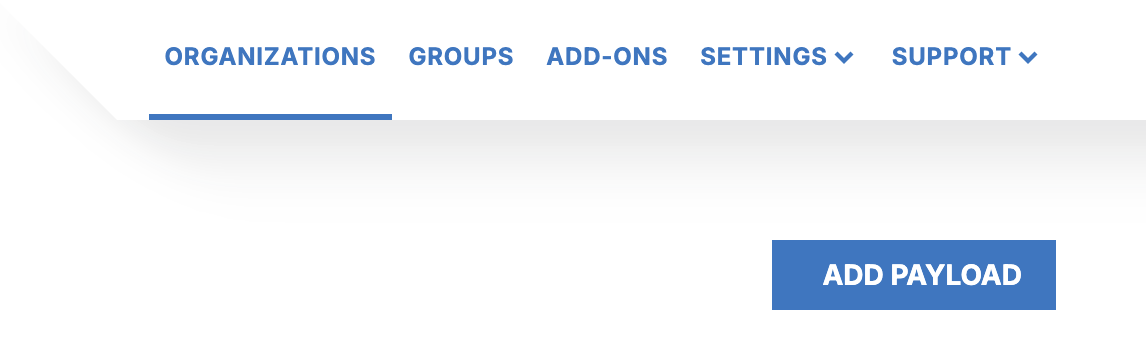
Name it something like deploy_cyber_triage_collector.ps1 (the name of the script)
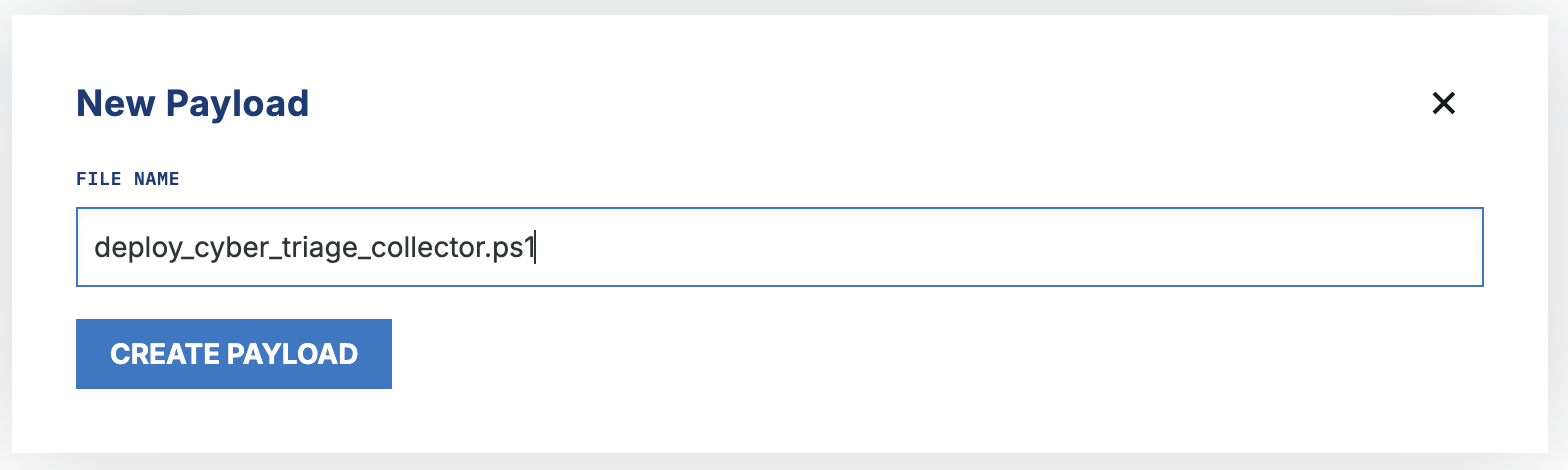
Upload the edited PS1 script
It is now ready to be used.
NOTE: We have not found a way to upload configuration files as a Payload.
7.1.3.3. Run the Collector Payload¶
When you need to collect from an endpoint, then perform the following:
Select the host that you want to collect from
Choose “Console” for that host
Type in:
run --payload-name deploy_cyber_triage_collector.ps1 --interpreter powershell --is-ignore-cert
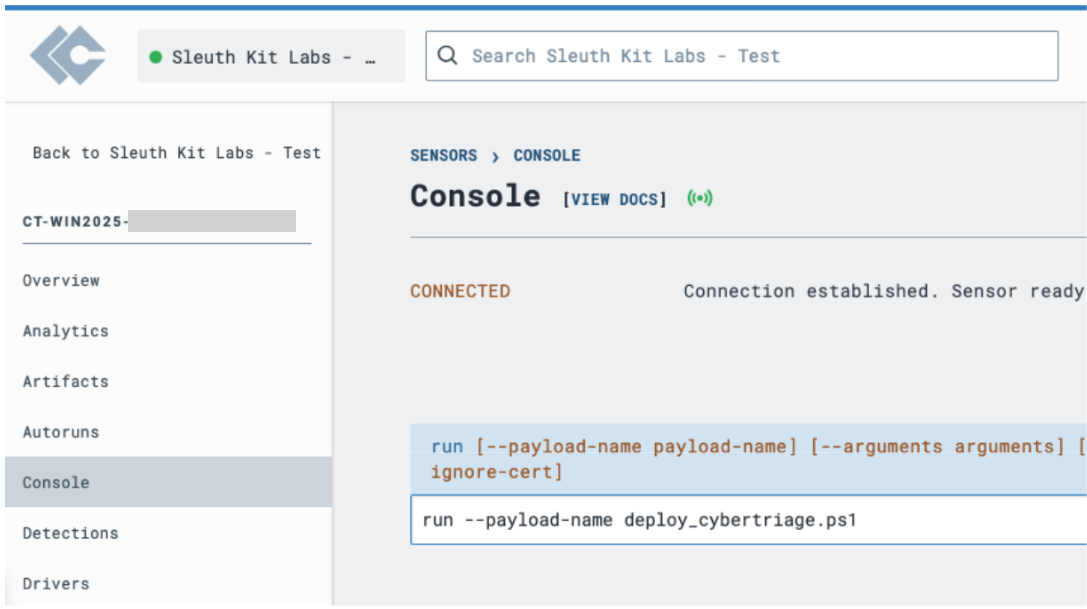
You can also supply Deployer script arguments if you give the ‘run’ command the ‘–arguments’ argument.
7.1.3.4. Getting Locally Saved Collector Output¶
If you saved the Collector output to a file, you can retrieve it from the console.
You need to determine how many file parts the Collector created. You can use ‘dir_list’ for that.
dir_list “c:\windows\temp\file.json.*"
For each of those files, you can download with ‘artifact_get’:
artifact_get --file “C:\windows\temp\file.json.gz”
This command will either return a ‘Error: 200’ on success or you may get a timeout if the file is large (but the file is generally still downloaded).
This will cause the file to be saved under the ‘Artifacts’ tab for the host.
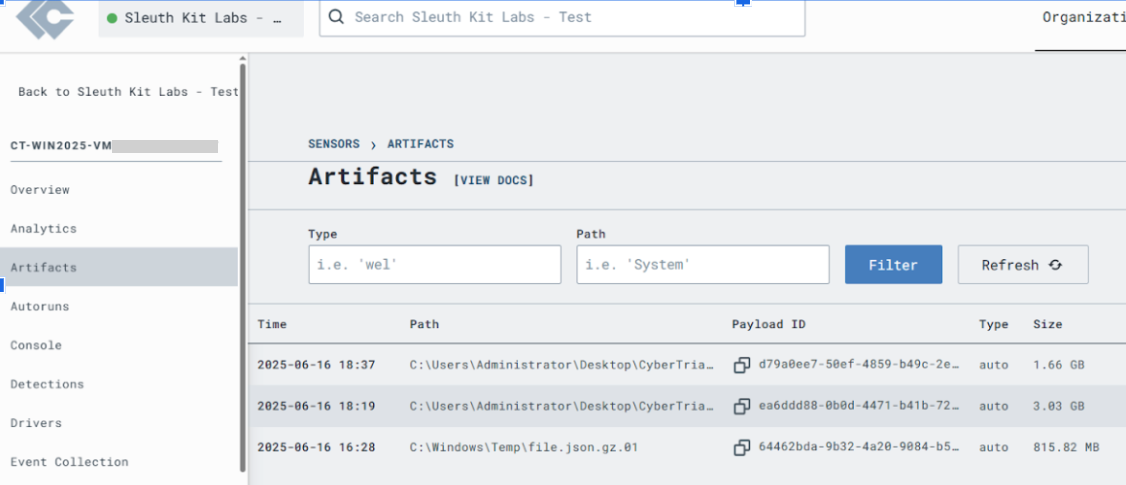
The file will be downloaded based on the Payload ID, but you can rename it to its original name (file.json.gz, for example).