14. Application Maintenance¶
14.1. Detection by Antivirus and EDR¶
Cyber Triage’s collection tool, named the Collector, can be falsely identified by antivirus and Endpoint Detection and Response (EDR) systems as being malicious.
Notably:
The CyberTriageCLI.exe program can be flagged when it is run on the target system or when it is run from your analysis system and being pointed to disk images or logical files.
The CyberTriageGUI.exe program can be flagged when it is run on the target system. It uses a graphical interface framework that attackers have started to also use.
Observations of this behavior will include:
A collection will stop early. Error messages in the JSON output can sometimes indicate if an error happened and it gracefully shut down early or was quickly terminated. If the process was killed by the EDR, then no graceful shutdown message will exist.
The local executable will not exist when you try to add a disk image or logical file set. To fix this, you must re-install Cyber Triage.
We recommend that you add the hashes of these tools to your goodlist on your EDR. The SHA256 value is given in the release notes, as can been seen on the History.
14.2. Backup and Recovery¶
It’s important to make sure your Cyber Triage® data is backed up. This section outlines the key concepts for that. The procedures outlined in this section assume that the backed up data will be restored to the same versions of Cyber Triage and, if applicable, PostgreSQL.
14.2.1. Data Folder¶
All versions save a lot of data to the “data folder”, which by default is in the AppData\Local\cybertriage folder for the user that Cyber Triage® is running as. This directory should be backed up.
You can see the specific path in the General tab of the Options panel.
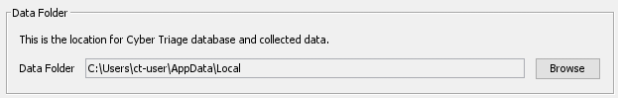
Note that it is possible to change the data folder (as outlined in Changing Where Data is Stored). If you do that, ensure the new location is also backed up.
The “SessionFiles” subfolder will contain copies of previously imported hosts. You can exclude these from the backup to save space.
14.2.2. PostgreSQL¶
If you have a Team deployment with PostgreSQL, then refer to its standard procedures for updating (including security patches) and backing up the PostgreSQL databases.
14.3. Reducing Data Folder Size¶
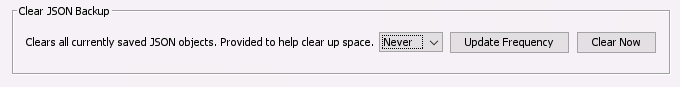
Cyber Triage stores copies of previously imported hosts in the “SessionFiles” folder in the “data folder”. These exist to ensure that you can reload data that comes in from over the network in case of corruption or crash.
You can configure Cyber Triage to periodically delete old copies of these files. These settings are available in the General tab in the Options panel.
14.4. Team Security Monitoring¶
The Team Server has network ports that are always listening. You can review the log files for brute force attempts to guess the security tokens.
The ‘rest-api.log’ file will have errors when an incorrect token is used or non-existent host or incident names are used.
For example:
ERROR [11:23:01.522] [xx-85 - POST /api/app-config/validate-credentials] c.b.d.c.c.c.ConfigManagerServerImpl - AUTHENTICATION FAILURE. Reason: invalid user credentials - userId or password does not match.