6. Incident Analysis¶
Cyber Triage offers several methods to analyze incident-level data from the hosts that were added to it. You can find these features from the Incident Dashboard when you open an incident.
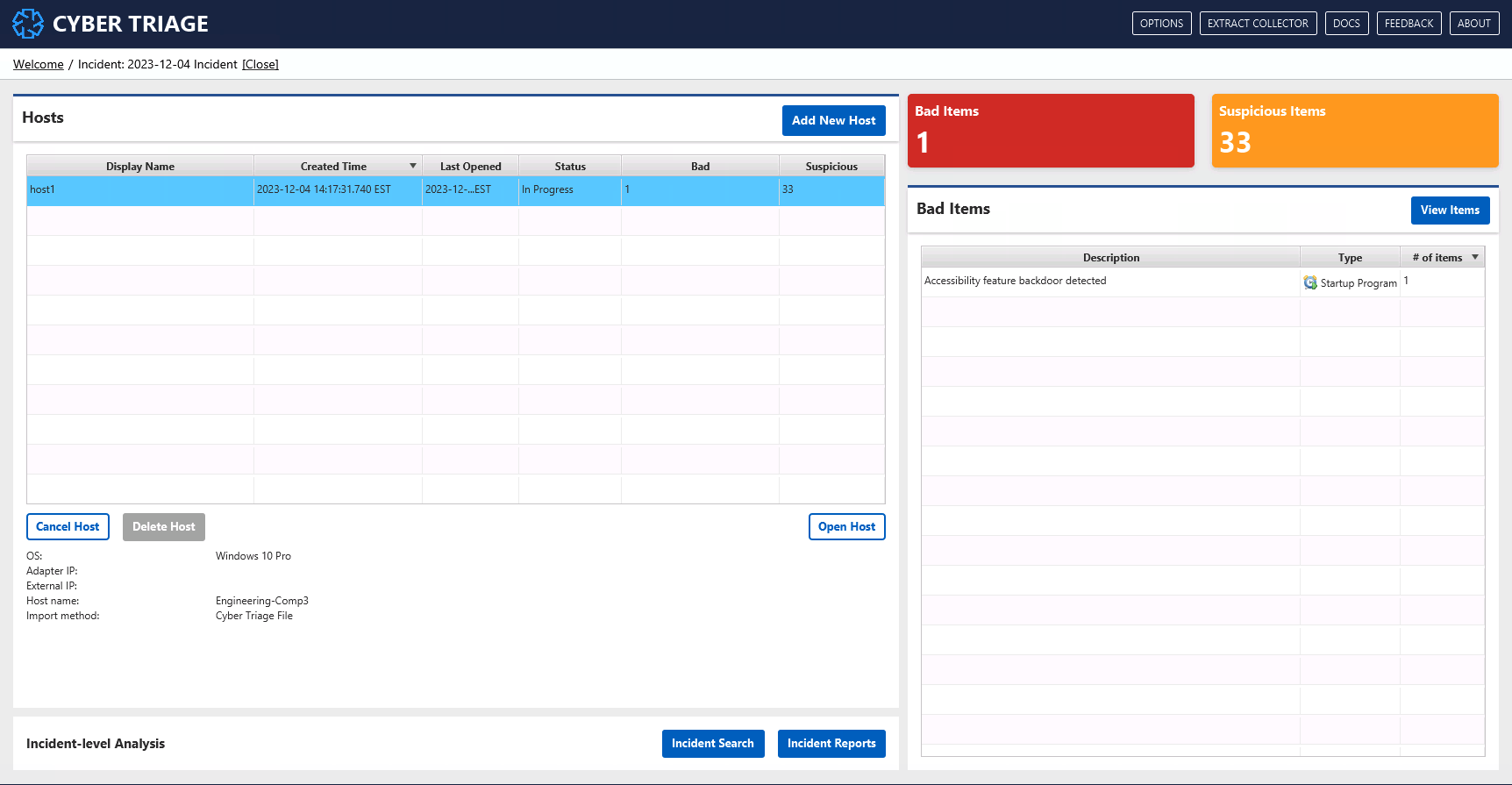
6.1. Hosts Table¶
The hosts table shows all hosts that have been added to the incident, their status, and number of bad items.
You can use this table when analyzing an incident to focus on hosts that have not yet been reviewed and that have high numbers of bad or suspicious. items.
6.2. Bad Items¶
The “Bad Items” table on the right-hand side shows the unique bad items in the incident. If the same item is in multiple hosts, it will be shown only once.
You can use this table to get an idea of what types of bad things are known so far in the incident.
Pressing the “View Items” button there will bring you to the “Notable Items” view that shows each bad item.
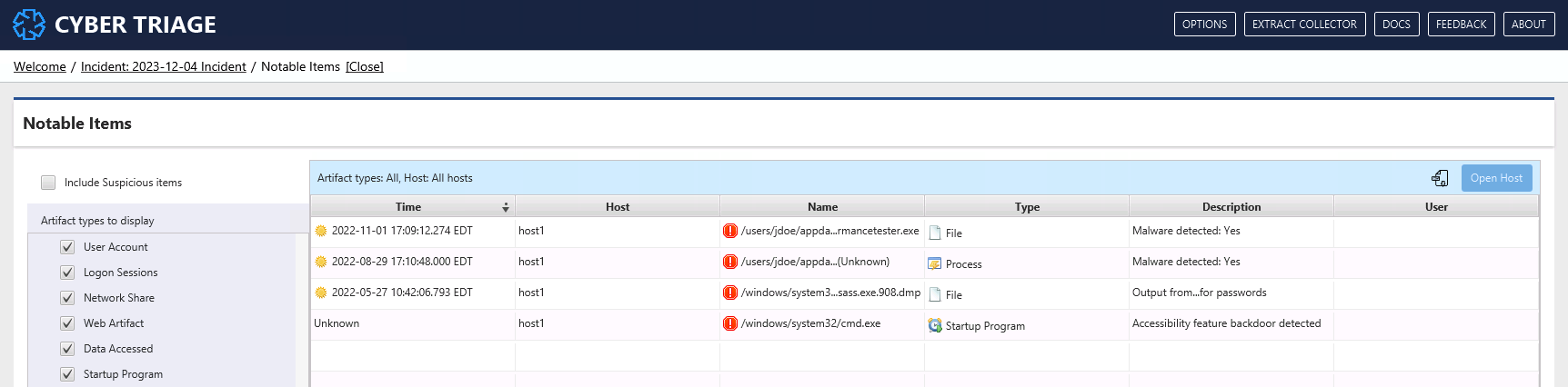
From here, you can use filters on the left to include suspicious items, remove noisy hosts, and data types.
You can also sort here (the default) to create a timeline of bad items across the incident.
From this view, you can press “Open Host” to see more about what happened on the host. That brings you to the UIs that were shown in Analyzing The Host Data.
6.3. Incident Search¶
The “Incident Search” button on the Incident Dashboard allows you to search all host data. There are two forms of search:
IOC Search: Search for text in any artifact metadata.
Advanced Search: Search for a specific type of artifact across all hosts that meet your criteria, such as date ranges.
6.3.1. IOC Search¶
IOC Search allows you to search for text or hash values in any artifact in any host. This is the same feature as the host-level search (see File and Artifact Search).
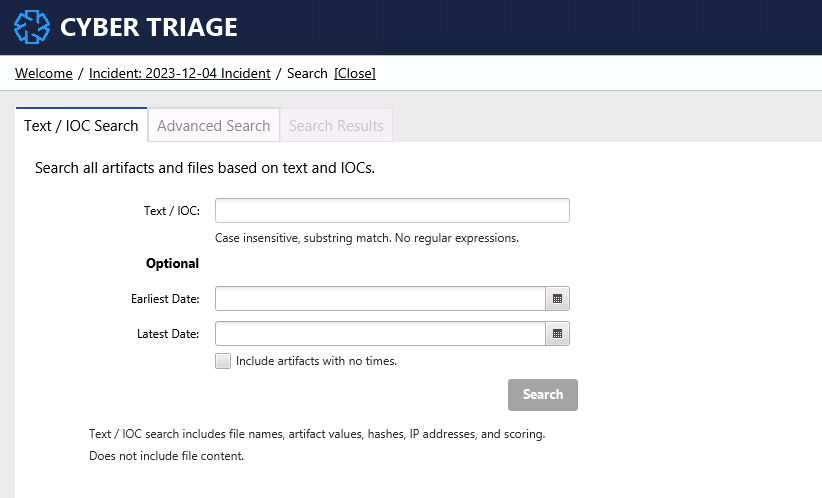
You can enter a text string in the above dialog and artifact metadata will be searched. Note that this is not a full text search of all file content. Metadata only.
This can be slow on large incidents.
A maximum of 5,000 results will be shown. If you hit this limit with your search, consider adding in more date limits.
6.3.2. Advanced Search¶
The second form of search is restricted to a specific type of artifact, such as Process or Logon. You can use this search to look for activity related to something you saw on another host.
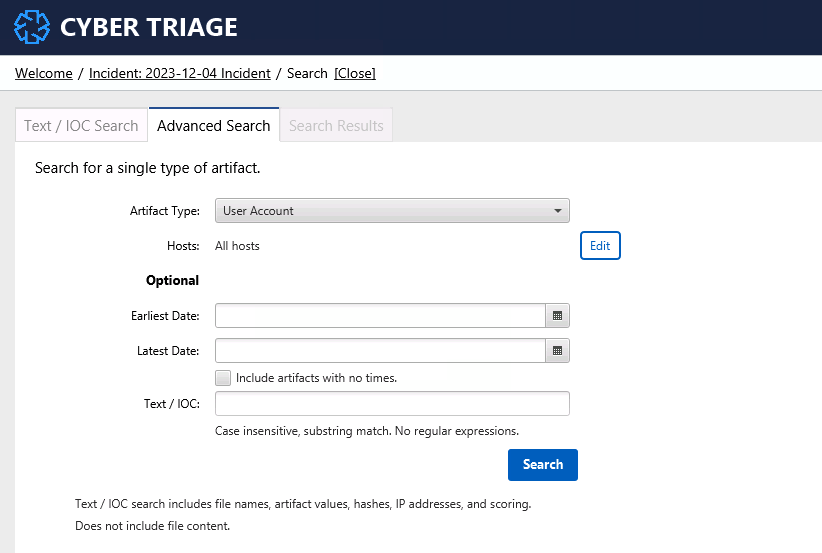
For example, you may want to search for all other logons in the same time frame as a lot of attacker activity. This could help you pinpoint other hosts to start investigating.
A maximum of 5,000 results will be shown. If you hit this limit with your search, consider adding in more date limits.