7.2.1. Microsoft Defender Integration¶
Cyber Triage can integrate with Defender for Endpoint in two ways:
The Defender agents can be used to deploy the Collector. See Windows Defender-based Collections for details.
- Defender telemetry can be imported via either API or CSV.
See below for configuring the API access
See Add EDR Telemetry Data for how to import the data
7.2.1.1. Configure Defender API Access¶
7.2.1.1.1. Create an Azure App¶
To access the data via an API, you need to create credentials by making an “App”. You can find the instructions on the Microsoft Site.
The basic process is:
Create the App within Microsoft Entra
- Give it Defender Graph API permissions:
SecurityAlert.Read.All
ThreatHunting.Read.All
Generate a ‘client secret’
- At the end of this process, you will need to know:
Client ID / Application ID
Client Secret
Tenant ID / Directory ID
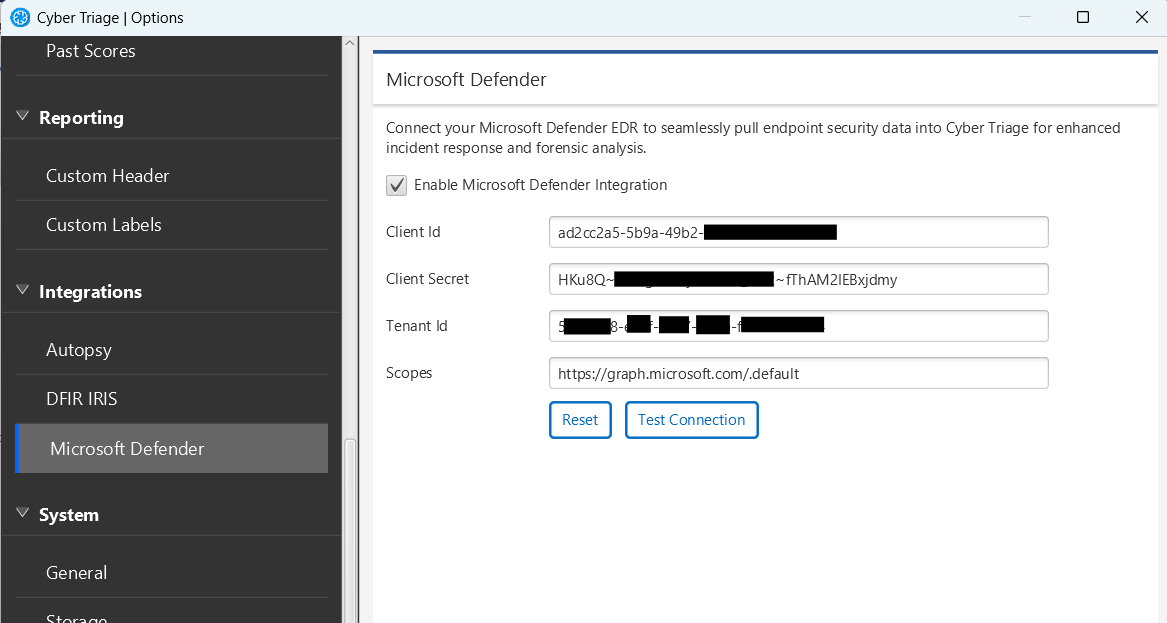
7.2.1.1.2. Add API Credentials into Cyber Triage¶
Once you’ve created the App, you can configure the tokens in Cyber Triage.
Go to the options panel and choose “Integrations / Microsoft Defender”.
Enter in the Client ID, Client Secret, and Tenant ID.
Press Test Connection to verify Cyber Triage can talk to the server.
7.2.1.2. Export Defender CSV Telemetry¶
To export telemetry data so that it can be imported into Cyber Triage:
Pick the device you want to analyze
Select the “Timeline” tab and, if needed, navigate to the relevant time range
Press the Export button
This will save 7 days of activity to your local system.
You can repeat this process by moving the timeline to a different 7-day range and exporting again. Cyber Triage can import multiple CSV files.