8. Configuring a Team Environment¶
This section outlines the installation and configuration of Cyber Triage® Team, which is a client-server deployment with one server and one or more clients. Only one instance of Cyber Triage® can run on a system at a time, so this means you will need at least two computers.
8.1. Architecture¶
There are three components of a Cyber Triage® Team cluster:
Cyber Triage® Server: Where the processing and analysis occurs. This contains the REST API used by clients and other integrations.
Cyber Triage® Clients: Runs on examiner systems and interacts with the Cyber Triage® Server.
Database: Where the collected data is stored. There are a few options for this, which are addressed in the next section. One main concept though is that the database can run on either the same host as the server or on its own host.
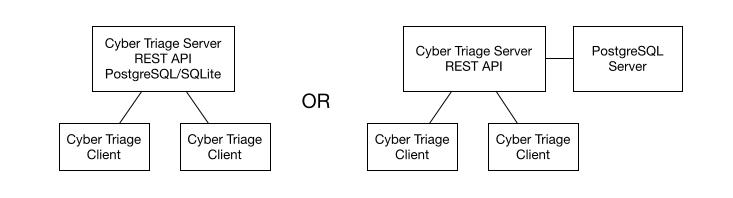
Cyber Triage® Team cluster¶
All three components should be on the same private network. The Cyber Triage server and database should not be on a public-facing address. You can run Cyber Triage in a cloud environment, but all components should be within a Virtual Private Cloud (VPC).
8.1.1. Database Options¶
There are three database options in a Team cluster:
SQLite: The server can create local SQLite databases for each incident. This is sufficient for evaluation purposes because it requires no additional configuration. However, its performance will be limited as the number of incidents and ingested hosts increase within Cyber Triage. SQLite allows only one write at a time (and blocks reads during a write), so it will not perform well with multiple hosts being analyzed at the same time.
PostgreSQL on the same host as the server: With this setup, a single computer will have both the Cyber Triage Server and PostgreSQL. This setup minimizes the number of hosts to maintain and can be more secure because PostgreSQL access can be restricted to the local host. However, this scenario requires more memory and storage resources on a single host. Refer to the following section to test your systems’s PostgreSQL speed.
PostgreSQL on its own host: Lastly, you can run PostgreSQL on its own dedicated host (Windows or Linux) or use a managed PostgreSQL service if you are running in a cloud VPC. This can be useful if you do not have a single server with enough resources for both, if you want to use Linux for PostgreSQL, etc.
We recommend that you start your production environment with PostgreSQL on the same host as the Cyber Triage Server.
Warning
There is NO data migration path between SQLite and PostgreSQL.
If you are going to run Cyber Triage in a cloud VPC, then you can refer to blog posts that we did where we tested various managed PostgreSQL services. For example, here is the post about AWS.
8.1.2. Testing PostgreSQL Speed¶
When choosing between running PostgreSQL on its own server versus running alongside Cyber Triage®, you can measure the PostgreSQL performance using pgbench. We have found this is much more reliable than focusing on hardware specs. We recommend that your PostgreSQL installation is able to get at least 4250 transactions per second (TPS).
You can start by installing PostgreSQL on the same server as Cyber Triage® (as outlined below). You can then use the following commands to measure the TPS. If they are too slow, then you can consider setting up a dedicated server.
- Setup the test by running the following. It will prompt you for the superuser password you entered during the installation.
C:\Program Files\PostgreSQL\13\bin\pgbench -U postgres -i -s 50 postgres
- Run the test:
C:\Program Files\PostgreSQL\13\bin\pgbench -U postgres -c 5 -j 2 -t 1000 postgres
Note
The final values may change in between runs, so you might want to run it a few times.
8.2. Team Software Requirements¶
Cyber Triage MSI installer.
PsExec 2.2(or newer) if you want to push the collection tool to remote hosts over the network.PostgreSQL 13 (or newer) For production environments using PostgreSQL (not required for basic evaluation)
8.3. Team Hardware Requirements¶
Team Server: 64-bit version of Windows Server, 4+ cores, and 250GB+ of free hard drive space.
Server only: 16GB+ of RAM
Server and PostgreSQL: 32GB+ of RAM
Team Clients: 64-bit version of Windows 7 or newer, 8GB+ of RAM, 4+ cores, and 50GB+ of free hard drive space.
Optional Separate PostgreSQL Server: 16GB+ of RAM, 4+ cores, and 250GB+ of free hard drive space. Either Linux or Windows.
We recommend using SSD storage for best performance.
8.4. Installing and Configuring PostgreSQL¶
If you are going to use PostgreSQL, then the following sections outline its installation and configuration on Windows.
8.4.1. PostgreSQL Installation¶
PostgreSQL can be installed in a variety of ways, including with installers, package managers, or containers such as Docker.
The easiest method for most Cyber Triage® users will be to use a PostgreSQL windows installer and choose the default settings. You do not need to use StackBuilder if it prompts you to.
Note
Data Folder: The default is inside of the PostgreSQL installation folder.
Superuser Password: You’ll need this to configure the database.
At the end of the Windows installer process, PostgreSQL will be running as a service as the Network Service account.
If you wanted to test the PostgreSQL speed as outlined in Testing PostgreSQL Speed, you can do that now before doing further configuration.
8.4.2. PostgreSQL Configuration¶
There are several settings that must be changed from the default installation. After you have made these changes, you should reboot the system for them to all take effect.
8.4.2.1. Create Database User¶
A special user will need to be created for the Cyber Triage® Server to access the database. We’ll use the name cyber_triage.
From a Windows Command Prompt run:
C:\Program Files\PostgreSQL\13\bin\psql -U postgres postgres
You will be prompted for the superuser password you entered during the installation.
You will next get a
postgres=#prompt. To create the user enter the following code below and replaceChangeMeASAPwith a real password.
Ensure you record the password because you will need to enter it into the Cyber Triage® server.CREATE ROLE cyber_triage PASSWORD 'ChangeMeASAP' CREATEDB LOGIN;
Type
\qto exit prompt.
8.4.2.2. Basic Configuration Changes¶
There are several settings that we suggest making to improve performance and enable logging to make debugging problems easier.
Note
These are all oriented around a Windows installation and a Linux deployment have other settings that will make it more optimal.
Open the following file in a text editor:
C:\Program Files\PostgreSQL\13\data\postgresql.conf
The following settings should be changed or uncommented (by removing the leading #):
- Edit the maximum number of connections:
max_connections = 200
- Increase the value of the buffer setting:
shared_buffers = 512MB
- Enable huge_pages by uncommenting this line:
huge_pages = try
- Uncomment the following performance-oriented lines and change the default values:
temp_buffers = 80MB shared_memory_type = windows fsync = off synchronous_commit = off
Uncomment and change the effective cache size based on the amount of RAM available. We recommend the value be 50% of the total RAM.
effective_cache_size = 16GB
- Uncomment the following log-oriented lines and change the default values:
log_min_duration_statement = 300 log_lock_waits = on
This file also allows you to restrict access to the database from other hosts.
- If PostgreSQL is on the same host as the Cyber Triage® server, then edit the
listen_addressline to the following: listen_addresses = 'localhost'
- If PostgreSQL is on the same host as the Cyber Triage® server, then edit the
- If PostgreSQL is on a different host, then confirm that the line is:
listen_addresses = '*'
8.4.2.3. Lock Pages in Memory Setting¶
If you are running PostgreSQL on a Windows system, we recommend that you also enable the Lock Pages in Memory setting for the Windows user that the service will be running as. By default, this is the Network Service account.
Open the Local Group Policy Editor
Navigate to Local Computer Policy -> Windows Settings -> Security Settings -> Local Policies -> User Rights Assignment
Select the Local pages in memory item and double click on it.
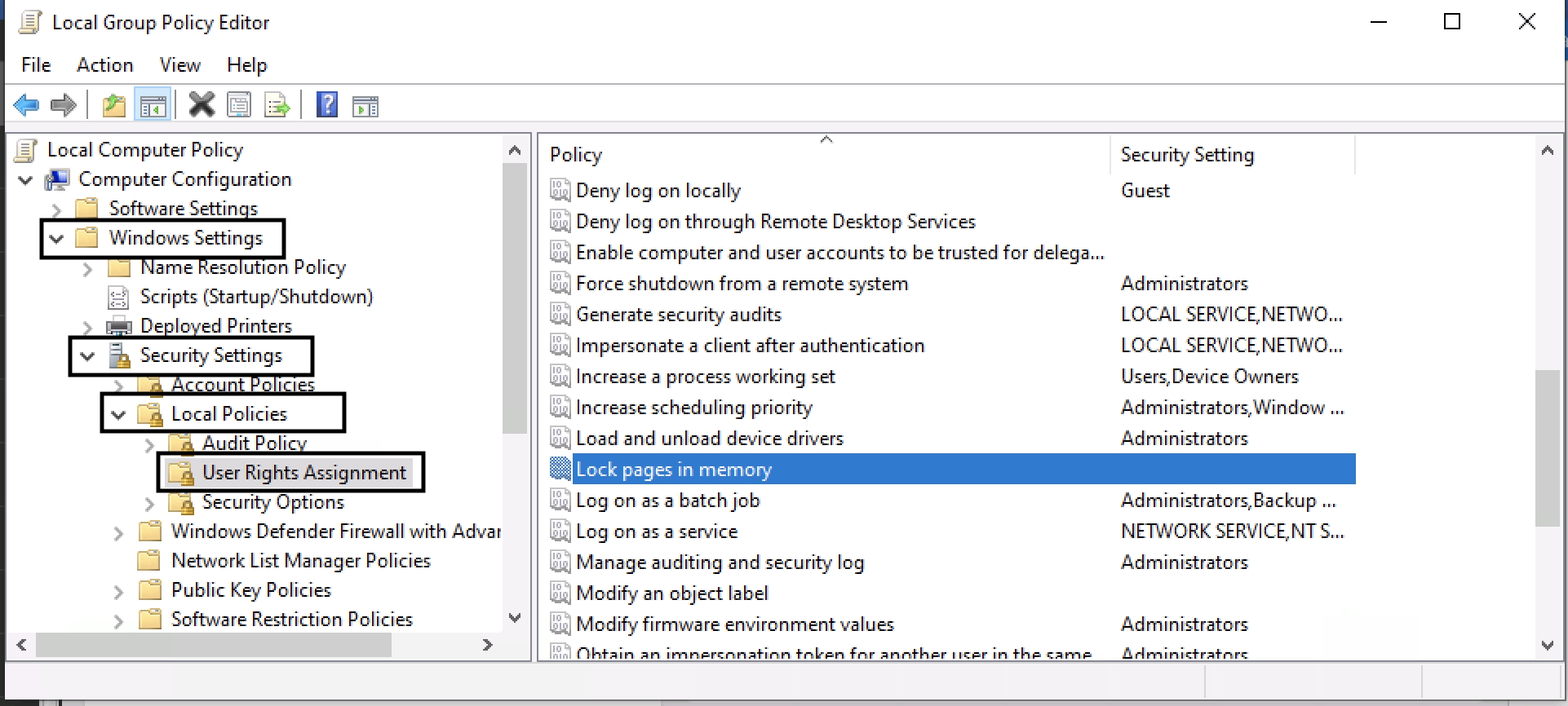
Local Group Policy Editor¶
Add the user that the PostgreSQL service will be running as (i.e. Network Service)
8.4.2.4. Dedicated PostgreSQL Server Changes¶
If you are running PostgreSQL Server on a system different from the Cyber Triage® server, you’ll need to make an additional change.
Open the following in a text editor:
C:\Program Files\PostgreSQL\13\data\pg_hba.conf
Add a rule to the bottom similar to:
host all cyber_triage 10.10.10.10/32 scram-sha-256
Update the above rule based on:
IP Address of the Cyber Triage® Server
The
password_encryptionvalue in the postgresql.conf file.
8.4.2.5. Restart The Host¶
After all the above configuration changes, restart the computer so that the service and database settings take effect.
8.5. Configuring The Cyber Triage Server¶
The Cyber Triage® server will need to be running whenever you want to use any of the Cyber Triage® clients to create or open sessions. It will be receiving the network connections from the various collection tools and will be performing all of the automated analysis.
The installation steps for the server (and client) start the same way as the standard version, which are outlined in Standard Installation. Namely, to launch the .msi installer and choose the default options.
When prompted for a license, choose the license file that you received that has _server in the name.
When Cyber Triage® is open:
Open the Options panel and choose the Deployment Mode tab. Change the mode to Team - Server. If you do not have this option, then you did not supply a Team license key.
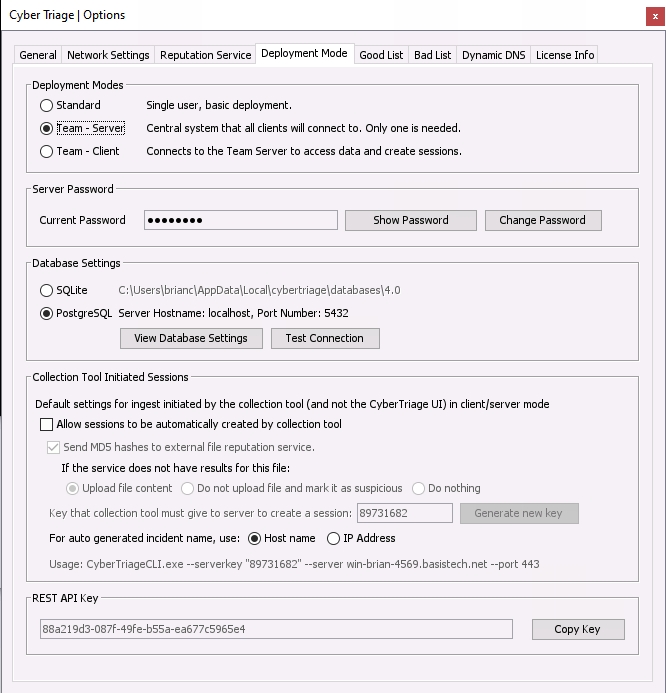
Options (Deployment Mode Tab)¶
In the Server Password section, press the Change Password button and pick a password that clients will use to connect to the server. You will need the new password when you configure each client, so write it down somewhere safe or make sure you remember it.
In the Database Setting section, either keep it as SQLite or enter in the PostgreSQL information by pressing the View Database Settings button. Use
localhostas the host if you are running the server on the same system as the server.
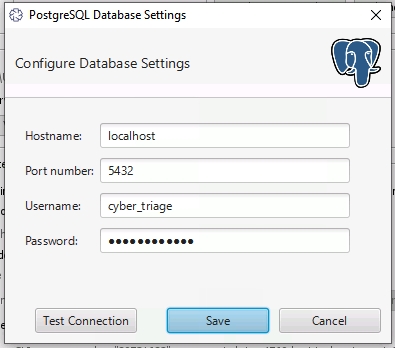
PostgreSQL Database Settings¶
Press OK and it will restart Cyber Triage®.
When it restarts, your host firewall software may ask permission to open ports. These are required for the server to operate.
When running as a Server, the Cyber Triage® interface will only allow you to go to the options panel or extract the collection tool. You cannot create or open sessions directly on the server.
Before configuring clients, go the License Info section of the Options panel and record the short TLS certificate hash from the self-signed certificate created on that system. The client installation will prompt you to ensure it is the right hash.
If you have a TLS intercept proxy in between the Server and the Clients, configure Cyber Triage with the proxy’s certificate. See Internal Intercept Proxies.
8.6. Configuring the Cyber Triage Clients¶
Cyber Triage® clients can be installed on any analysis system. The responder will use the client to create and open incidents.
To configure each Cyber Triage® client:
Install Cyber Triage® using the same MSI as you used for the Server.
Supply the same appropriate client license key.
Open the Options panel using the button in the upper right and choose the Deployment Mode tab.
- Choose Team - Client.
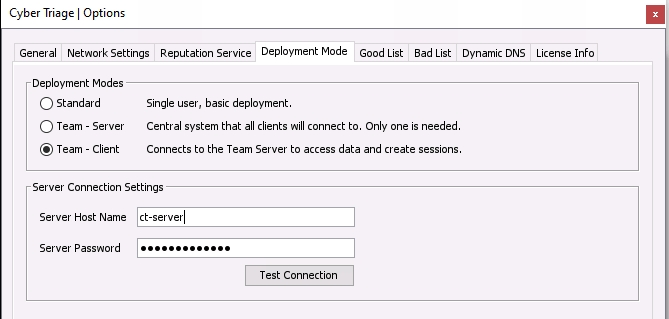
Options (Deployment Mode Tab)¶
Enter the hostname or IP address of the server and the Server Password that you configured on the Server. Press the Test Connection button to ensure that the client can connect to the Server.
You will be prompted to confirm the TLS certificate that was received from the server. Compare the value displayed with the value on the Server, which you can get from the Options panel on the Server.
Press OK and Cyber Triage® will restart.
8.7. Team General Information¶
This section outlines general information for using Cyber Triage® Team:
Any client can open any session, even if it did not create the session.
Some functionality is currently more limited in a client-server deployment, such as the ability to cancel collections and malware analysis.
8.8. Configuring the Server to Run as a Service¶
You can also run the Team Server as a Windows service, which ensures that it runs when the computer starts and does not require a user to be always logged in.
8.8.1. Limitations¶
You need to run the service as a user account because the user must login to configure the Server.
To make changes to the Server, you will need to stop the service, launch Cyber Triage® as a user to make changes via the Options panel, close Cyber Triage®, and then start the service back up again.
8.8.2. Service Installation Instructions¶
- Stop and uninstall an existing Cyber Triage® service by opening a command prompt (with Admin priveledges) and running:
<Previous_CT_Location>\cybertriage\service\svcmgr.bat uninstall
Install and configure the Server using the steps outlined in Configuring The Cyber Triage Server. Also configure settings such as NSRL and Yara.
After the server is configured, close the application. Ensure that you do the configuration while logged in under the account that the service will run as. Otherwise, the configuration settings will not be available to the service.
- In a Admin command prompt, change to the new Cyber Triage® folder
cd C:\Program Files\Cyber Triage-3.0.0\cybertriage\service
- Install the service by running:
svcmgr.bat install
- Launch the Cyber Triage® Service Manager from the command prompt by typing:
CyberTriageServicew.exe
- Configure the user account via the Windows Service Manager after CyberTriageService.exe has created the service. This should be the same user account that was used to configure Cyber Triage®.
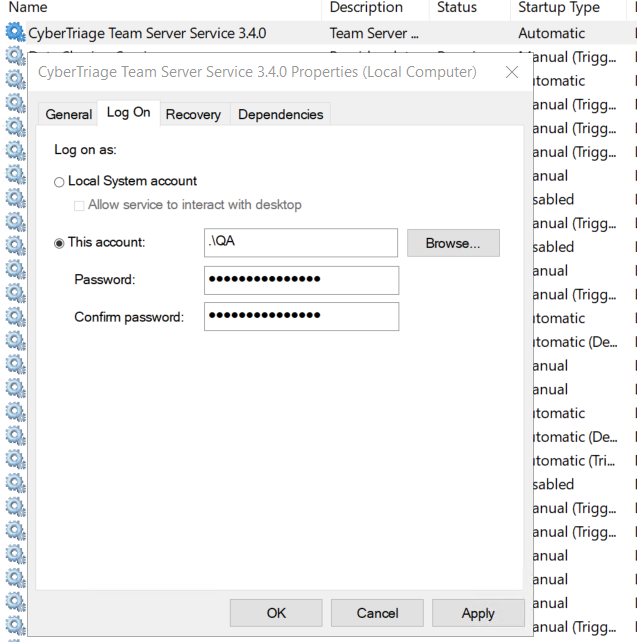
Team Server Log On Screen¶
Press Apply.
Either restart the server so that the service starts or press Start on the General Tab.
8.8.3. Verifying The Service¶
You can get basic status of the service by pointing a web browser at: https://SERVER_HOST_NAME:9443/api/admin/service-status
8.8.4. Making Changes to Service¶
To make configuration changes, you will need to stop the service, launch Cyber Triage®, make your changes, close the application, and then start the service again.
8.9. Configuring the Team-specific Features¶
8.9.1. Allow Collection Tool To Initiate Collections¶
By default, Cyber Triage listens for network connections only when initiated by a user. The Team Server can be configured to always listen for connections. Any connection without the secret key will be dropped.
This feature is useful when deploying the Collection Tool via EDR or other IT infrastructure.
To enable this feature, go to the “Deployment Mode” section of the options panel (on the server) and enable “Allow collections to be automatically created by collection tool”.
Choose the default malware scan settings and record the “key”. You’ll need that when you start the collections.
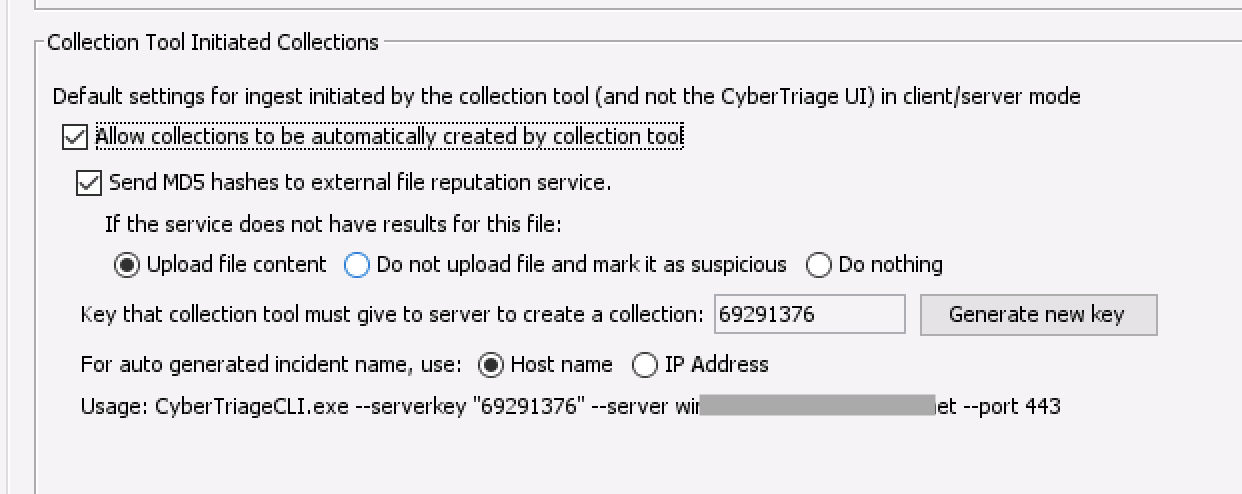
Refer to Deploy via EDR, PowerShell, WMI, etc. for steps on launching the Collection Tool.