1.2. UI Overview¶
This section provides a high-level overview of using the Cyber Triage user interface.
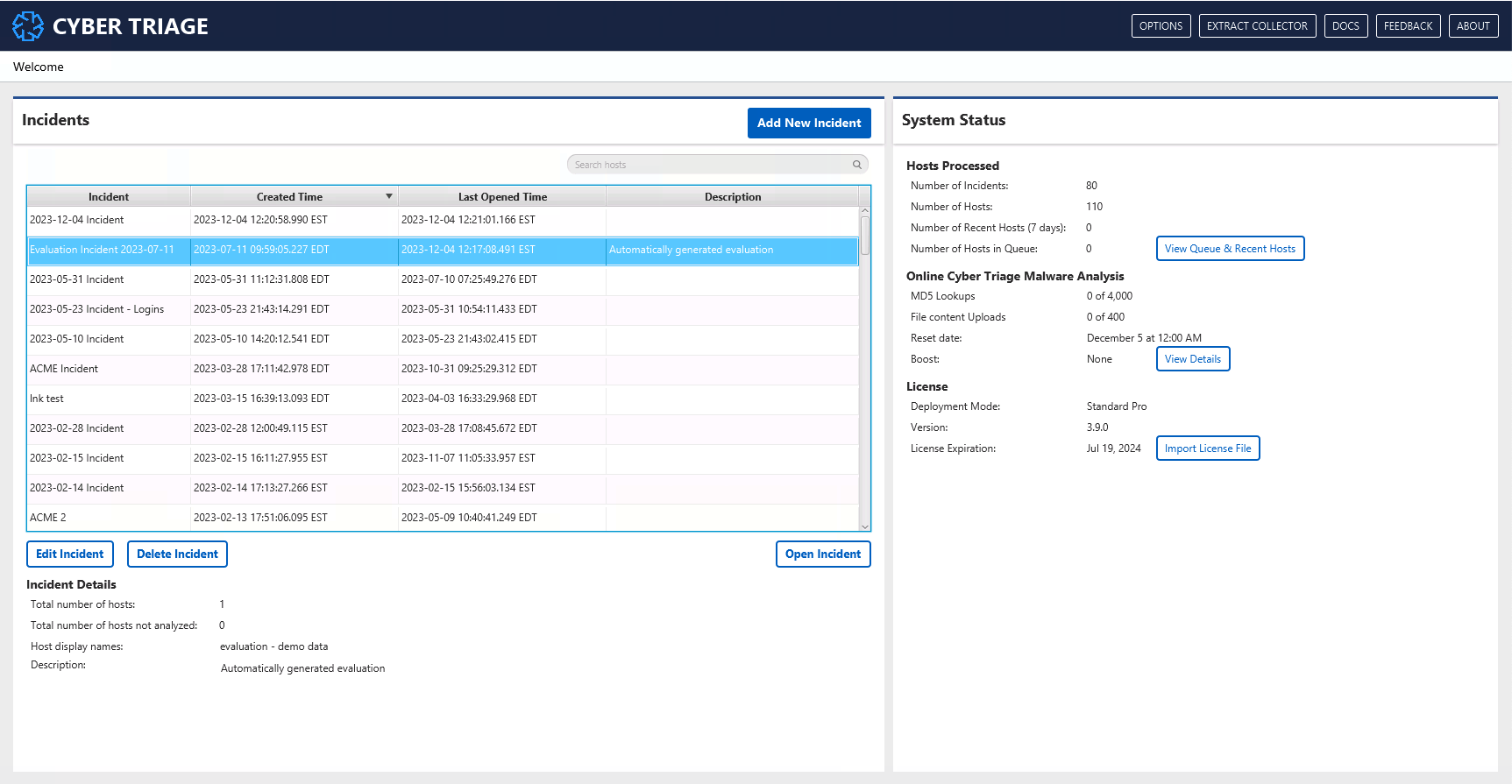
1.2.2. The Welcome Page¶
When you launch Cyber Triage, you’ll see the Welcome page (it was shown above).
From here, you can:
Add, delete, and edit incidents (see Incident Management)
Get an overview of system status on the right-hand side.
Use the top menu to get the collection tool, options panel, and provide feedback.
Search indicators from past incidents (see Global IOC Search)
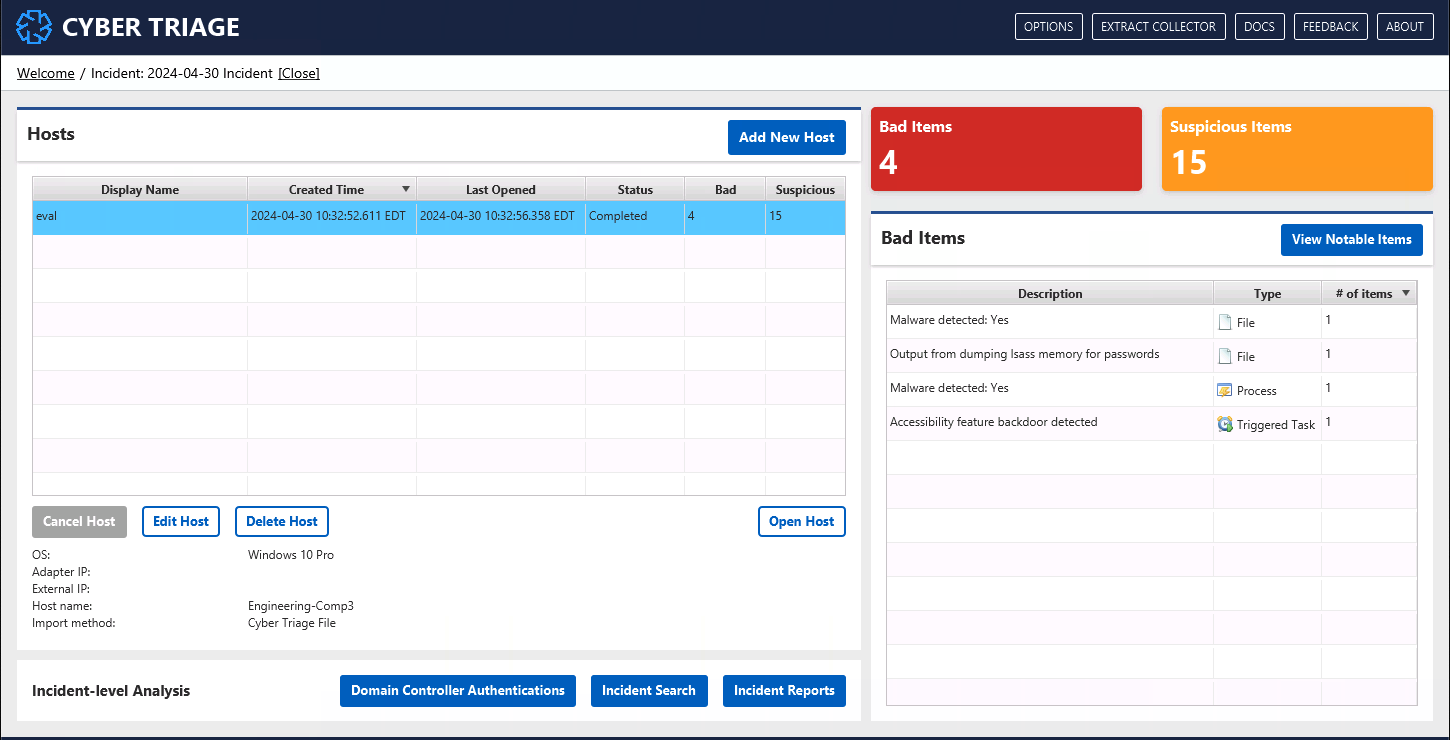
1.2.3. Incident Dashboard¶
When you have an incident open, the Incident Dashboard (shown above) is your starting point.
It allows you to:
Add and delete hosts in the incident
See progress of analysis on the hosts
Get an overview of bad items to decide which host to manually review
Review a timeline of bad items accross all hosts in hte incident
You can use this data to decide which host to open and examine.
Incident-level Examination provides more details about what kind of analysis can be performed from this UI.