2. UI and Configuration Basics¶
This section outlines the basics of the UI and various settings that you may need to change before adding data. Additional configuration of a Team deployment is covered in Team Installation and Configuration.
2.1. UI Basics¶
2.1.1. The Welcome Screen¶
When you launch Cyber Triage, you’ll get a screen such as this. This is the Welcome screen.
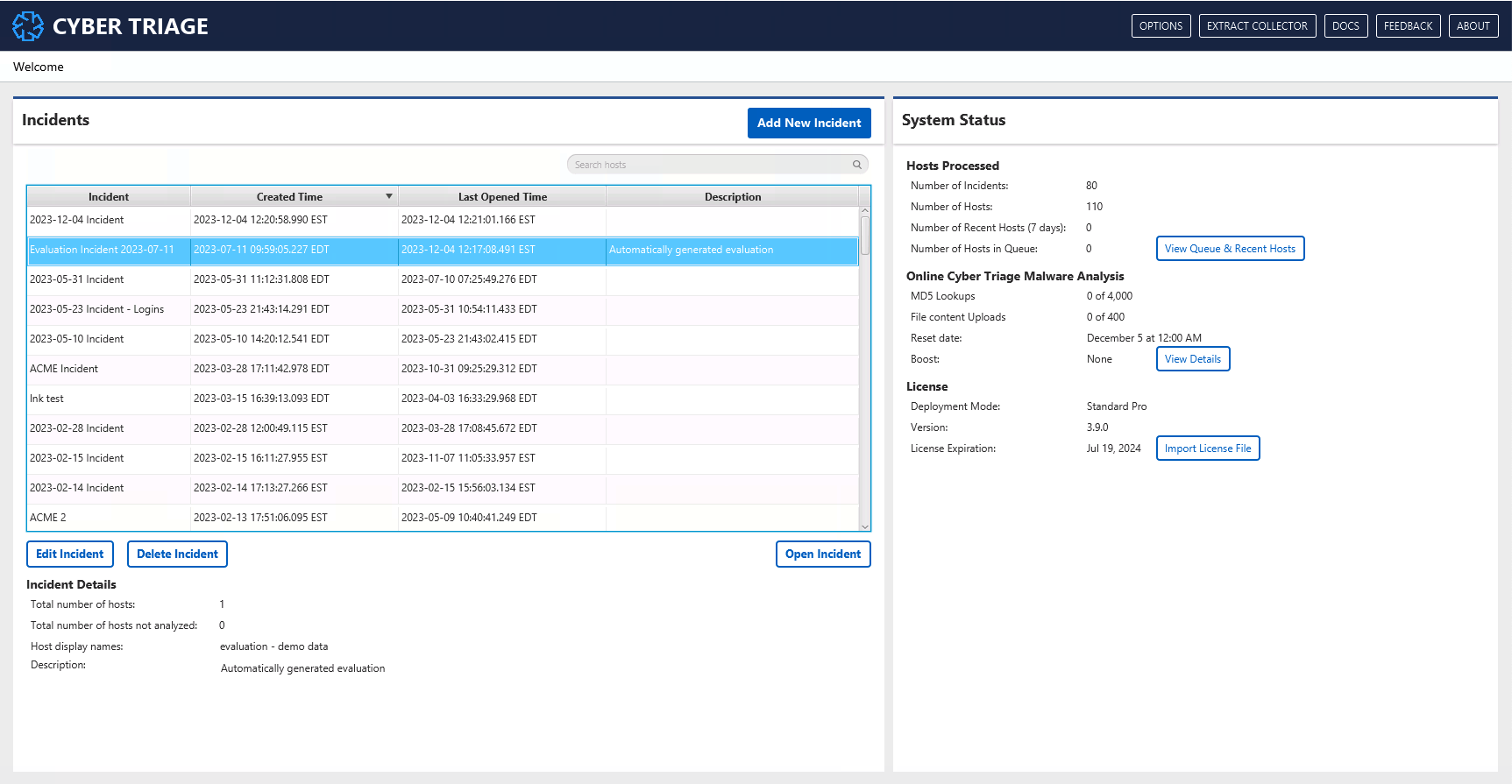
From here, you can: * Add, delete, and edit incidents (see Incident Management) * Get an overview of system status on the right-hand side. * Use the top menu to get the collection tool, options panel, and provide feedback.
2.2. Configuration Basics¶
In many cases, you can use Cyber Triage with no additional configuration. But, this section provides an overview of things to consider. Sections below provide the details for any that seem relevant to you.
If you plan to use the “Network - PsExec” feature of Cyber Triage that allows you to copy over the collection tool via PsExec, then refer to Configuring for Network - PsExec Collections.
If you plan to customize the files that the Collector will collect, then refer to Customize File Collection.
If you want to use your own Yara rules or edit the Good / Bad lists, then refer to Configure Yara Signatures or Configure Bad and Good Lists.
If your network restricts traffic based on destinations and ports, then refer to Network Traffic (Ports and Hosts Used) for details on what Cyber Triage needs.
If you have a TLS intercept proxy, then you need to configure Cyber Triage so that it validates that certificate. Refer to Internal Intercept Proxies.
2.2.1. Configuring for Network - PsExec Collections¶
Additional configuration is needed to use Network - PsExec collection (Network - PsExec). Namely
Configure PsExec
Ensure target is configured
NOTE: Microsoft has dropped support for Windows XP with the latest versions of PsExec. If you are still using Windows XP and require the Network - PsExec functionality, you will need to find an older version of PsExec (2.34 or earlier). Contact our support team if you need to use PsExec on XP systems.
2.2.1.1. Configure PsExec¶
Download PsTools
Unzip the PSTools.zip file to a folder on your computer.
Open the Cyber Triage Options panel from the opening Cyber Triage® window.
Navigate to the General tab.
Find the PsExec Settings area, choose the Browse button, and navigate to the folder that you extracted the contents into. Confirm that you read the PSTools End User License Agreement.
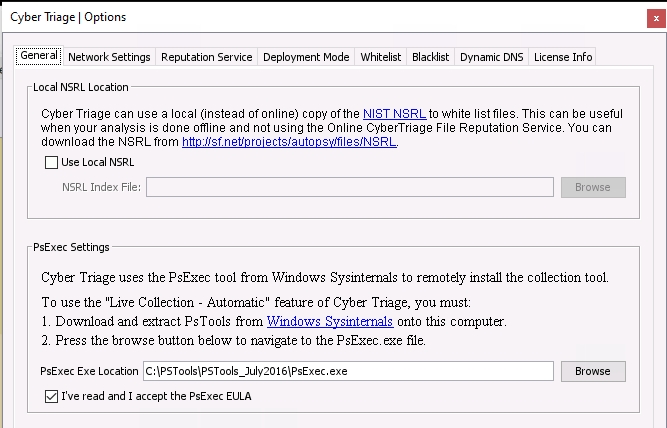
Configuring PsExec tool¶
2.2.1.2. Services Required on Target System¶
The target system for Network - PsExec must have file sharing enabled so that PsExec can copy over the Collector.
2.2.1.3. Enable Local Accounts¶
If you want to use a local account on the target system (instead of a domain account), then you’ll need to make a change from the default settings in order to use Network - PsExec.
Run the
regedit.exeWindows program on the target computer.Navigate to the
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Systemnode.Right click on the System node to add a REG_DWORD value with a name of
LocalAccountTokenFilterPolicy(no quotes) and a value of1.Either reboot the computer or restart the “Server” service (LanmanServer) and the “Workstation” service (LanmanWorkstation). Either of these will ensure the new policy is used.
2.2.2. Customize File Collection¶
You can collect additional files beyond what Cyber Triage already collects. This is useful when you want to make sure you get logs from a certain application or from indicators of a recent attack.
The following terms are used in this process
File Rule: A set of criteria that, when matched, will cause the file to be collected.
File Rule Set: A set of file rules. The file will be collected when any rule matches. You can organize rules in any way that makes sense for you.
2.2.2.1. Adding Custom File Collection Rules¶
To add a rule, go to the Options panel and chose “File Collection Rules”. Rules need to be in a set, so create a set if none exist or you want to organize the new rule differently than the others.
Create a new set with New Set. You need to give it a unique name and can optionally give it a description.
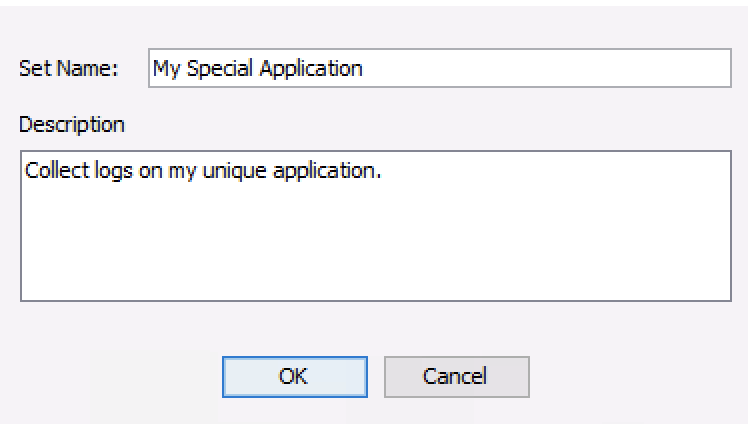
Add New File Set¶
Once the set is selected, you can add a rule to it with New Rule.
There are different types of rules, which have different performance impacts.
Exact Match: If the full path is specified (parent folder and file name), these are fast lookups since the Collector knows where to look.
Fuzzy Match: If only part of the parent folder or file name are specified, then the rule will be applied to each file in the system. This requires the full file system scan to occur.
A rule has the following fields:
A unique display name
File Name: Can be full name, empty, or have wild cards. Details are below.
Parent Folder: Can be full name, empty, or have wild cards. Details are below.
Max File Size: Allows you to ignore files that are too big to collect.
Max File Age: Allows you to optionally ignore files that are old and likely not relevant to a recent attack. This field is number of days and is applied to the file’s creation date.
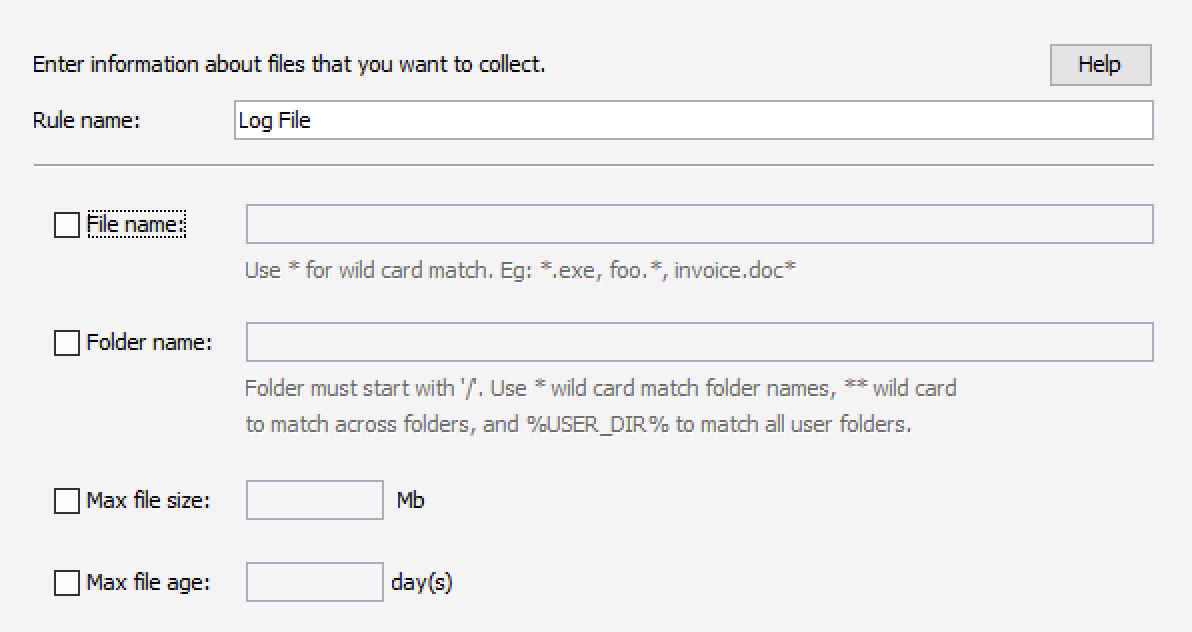
Add New File Rule¶
The following are more detailed requirements for file name:
This field is required if folder name is not specified
Comparison is case-insensitive.
Can not include any of the symbols that are not allowed in files: ‘:’, ‘>’, ‘<’, ‘:’, ‘”’, ‘/’, ‘', ‘?’
Can include one or more ‘*’ wild cards, which will match 0 or more of any character.
If no file name is given, all files in any directory matching the folder name will be collected (non-recursive).
The following are more detailed folder requirements:
This field is required if file name is not specified
Comparison is case-insensitive
Forward slash is used to separate folder names.
Can not include any of the symbols that are not allowed in files: ‘>’, ‘<’, ‘:’, ‘”’, ‘', ‘?’
Can start with %USER_DIR% to match the standard Windows user folders or any non-standard user folders extracted from the registry (if present).
If not using %USER_DIR% the path must start with a forward slash
Folder names should not end with a slash (unless using a single slash for the root folder)
- A ‘*’ wildcard that is not surrounded by forward slashes, will match 0 or more characters within a folder name.
/windows/system* will match /windows/system32
- A single ‘*’ wildcard surrounded by forward slashes will match any full folder name, but not recursively:
/Windows/*/notepad.exe will match /Windows/System32/notepad.exe
/Windows/*/notepad.exe will not match /Windows/System32/foo/notepad.exe
- A double ‘*’ wildcard surrounded by forward slashes will match any number of folder names:
/Windows/**/notepad.exe will match /Windows/System32/notepad.exe and /Windows/System32/foo/notepad.exe
If no folder name is given, all files with the specified file name will be collected.
Any wild card character will require the full file system scan. If you specify the full file name and the full folder path, then a targeted collection can be performed without the full file system scan.
Examples:
- To collect a specific log file (fast collection):
File Name: logfile.txt
Folder Name: /ProgramData/ApplicationName/Logs
- To collect all files in a specific folder newer than 60 days:
File Name: <Not specified>
Folder Name: /ProgramData/ApplicationName
Max File Age: 60
- To collect all executables in AppData:
File Name: *.exe
Folder Name: %USER_DIR%/AppData/**
2.2.2.2. Using Custom File Collection Rules¶
After you update or create rules, you may need to take additional steps to ensure the collections use them.
Network - PsExec: The Collector will download the latest version of the rules when the collection starts.
Network - Manual, Cyber Triage File: The rules are copied to the extracted folder. You’ll need to extract the Collector again to get the latest version of the rules.
KAPE, Disk Image, Logical Files: Local copies of the latest rules are used.