9. Generating Reports¶
Once your analysis is complete, you can generate a report to share with others. You can choose to make either a report of an individual host or the entire incident.
9.1. Host-level Reports¶
There are several types of host-level reports, which serve different needs. All of these can be created from the host dashboard.
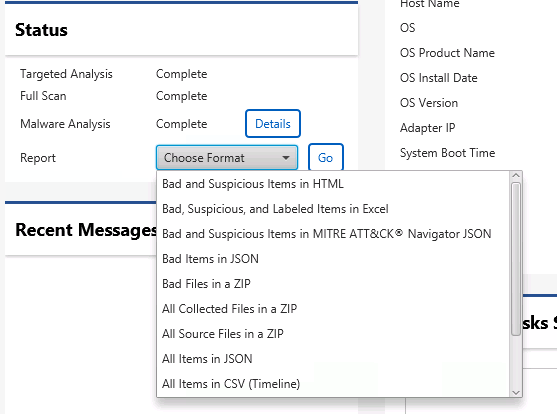
Types of Host-level Reports¶
We’ll review each of these. Some contain all data from a host and others contain only the bad and suspicious items.
Note that there are also incident-level reports that can be generated from the incident dashboard.
9.1.1. Bad and Suspicious in HTML Report¶
The “Bad and Suspicious Items in HTML” report is useful to share with other groups who want a human readable report. It contains the list of Bad and Suspicious items that were found on the system.
The report provides both a summary and a detailed view. The summary view provides basic information about each item and is organized into two tables: Bad and Suspicious. Selecting any item brings you to the detailed view that contains information such as MD5 hashes and time stamps.
Any comments that you added during the investigation will be shown in the report.
You can generate a PDF report based on the HTML report by using the Print feature in your web browser.
To add your company or agency logo to the report, use the Reporting Options tab within the Options Panel.
9.1.2. Bad, Suspicious, and Labelled in Excel¶
This report contains information similar to the HTML report, but in a format that is easier to copy and paste into your final report.
It has tabs for all bad items, all suspicious items, and tabs for each artifact type. In the artifact-specific tabs, all details should exist in different columns so that you can choose what to include in your final report.
9.1.3. Bad and Suspicious in MITRE ATT&CK¶
If you want to export the items that were scored as bad and suspicious and import them in the ATT&CK Navigator, then choose the MITRE ATT&CK report option. This produces a JSON that can be uploaded to the website and visualized.
9.1.4. Bad Items in a JSON Report¶
The “Bad Items in JSON” report will create a JSON file with just the items scored as Bad. You can use this to:
Do post processing or import into other systems
Import as “Bad Items” into other Cyber Triage installations.
9.1.5. Bad Files in a ZIP Report¶
The “Bad Files in a ZIP” module will make a single ZIP file with all files scored as bad. The ZIP file will have the password “infected”.
9.1.6. All Collected Files in a ZIP Report¶
This report will export all files that were imported into Cyber Triage.
The main use case for this is when you use the Cyber Triage Collector to copy data from a system and you then want to use another tool to analzye the data. Because the Collector output is JSON, then this is how you can get the data into a format that other tools use.
This ZIP file will have the same folder structure as the original files (i.e. “Windows\System32\Config”).
Note that these paths can be long and the default Windows extractor could have issues with the path lengths. Consider using 7Zip or another tool that supports long file paths to extract all of the files.
9.1.7. All Source Files in a Zip Report¶
This report is similar to the “All Collected Files in a ZIP” report except it only focuses on “source files”, which are the core files that get parsed to make artifacts. Such as:
Registry hives
Event logs
NOTE: These are the same files that you get from exporting files from the Collection Details panel.
9.1.8. All Items JSON Report¶
The “All Items JSON” report is useful for importing the results into another system, such as a SIEM. It is a JSON array with each element being a data item that was collected by Cyber Triage®. For example, the first entry could be for a Triggered Task Item or a Process entry.
There is a corresponding module that can import this into Splunk.
9.1.9. All Items in CSV (Timeline) Report¶
The “All Items in CSV (Timeline)” report contains one row per collected item. It can be imported into other timeline tools.
9.1.10. All Items in JSON Line (Timesketch) Report¶
The “All Items in JSONLine (Timesketch)” report creates a JSON file with all collected items. It can be imported into Timesketch or similar timeline tool.
9.1.11. All File SHA-256 Hashes as Text Report¶
The “All File SHA-256 Hashes as Text” module will create a text file with one line per file with a hash value. Hash values will exist for any file that was collected. This text file will contain both good and bad files.
9.1.12. All IPs as Text Report¶
The “All IPs as Text” module will create a text file with one line per IP address from the host. This includes IPs that were directly referenced in an artifact and IPs that Cyber Triage resolved from host names.
9.1.13. Extract Source Files¶
There used to be a report module that exported all source files (such as registry hives and event logs). That feature has been moved to the Collection Details panel. See Collection Details Panel for details.
9.2. Incident-level Reports¶
There are a subset of the above reports that you can also create at an incident level. They will often include the host name to differentiate the data.
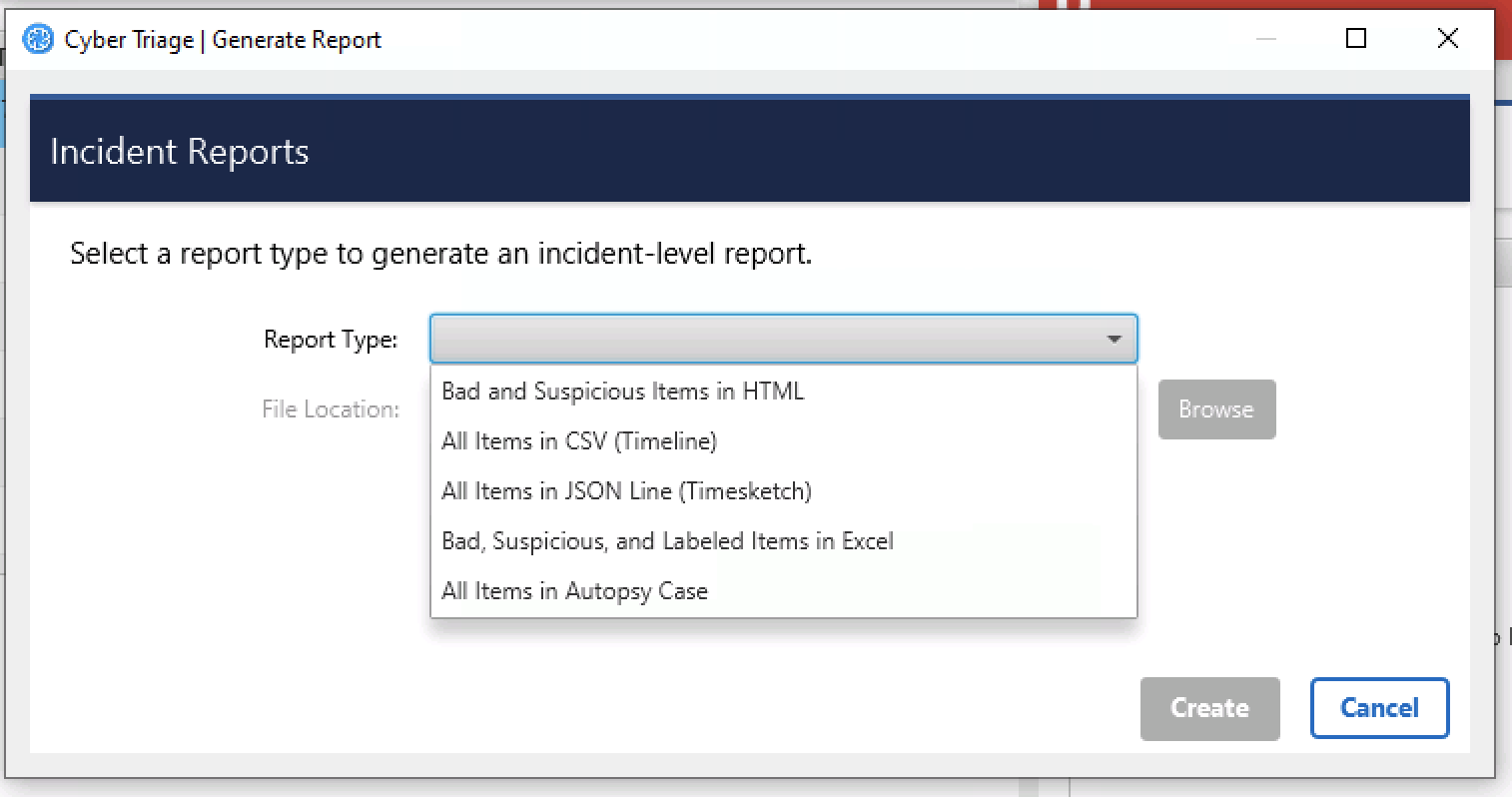
Types of Incident-level Reports¶
A unique incident-level report is “All Items in Autopsy Case”. This allows you to open the incident in Autopsy. More details of that can be found in Open a Cyber Triage Incident in Autopsy.