8. Threat Intelligence¶
Cyber Triage uses various sources of threat intelligence to score an item as good or bad. This section outlines the various methods and configurations that maybe required.
8.1. Malware Scanning¶
A Cyber Triage license comes with access to 40+ malware scanning engines through our Internet-based API. You will be prompted to use this for each host that you add. Our API is backed by Reversing Labs.
8.1.1. Initial Setup¶
The only setup steps required for this feature is to ensure that the computer running Cyber Triage can access the cloud-based API. Refer to Network Traffic (Ports and Hosts Used) for specific host names.
If you are offline, you can manually upload file hashes. See Advanced Configuration.
8.1.2. Per Host Configuration¶
When you add a host, you will prompted for what malware scanning settings you want to use. Refer to Malware Analysis Settings for more details.
8.1.3. What is Analyzed¶
Not all files from a host are sent for malware scanning. Only the following are:
Executable PE files, such as .exe and .dll files
Files not found in a local copy of the NSRL
Files not found in a local cache of previous lookups. These results can be flushed at any time and no guarantee is made about how long results will reside.
8.1.4. Types of Limits¶
Each license has a limit with respect to how many lookups and uploads can be done in a certain amount of time. The system has several dimensions to make it fair for all customers and to ensure you can finish examinations.
First, there are categories of analysis types, each with their own limits.
Each Hash lookup will count towards your hash lookup category
Each File upload and ImpHash Query will count towards the upload category.
Within each category, there are three types of limits to ensure you can analyze as many hosts as possible:
Licensed Base - Each Cyber Triage license comes with a maximum number of hash lookups and file uploads that reset either daily or weekly. These are hard limits. For example, Standard Pro comes with 4,000 hash lookups per day.
Licensed Flex - These allow you to go a bit over your licensed base limits to finish processing a host. Each license comes with 1,000 flex lookups to use over the course of a calendar month. You cannot analyze a host using only flex. You need to have at least one base or boost lookup to start and then flex will be used.
Boost - You can purchase additional lookups and file uploads when you have big incidents and need to temporarily go beyond your usual limits. See the next section for details on adding and purchasing Boost codes.
When a host is added, Cyber Triage uses the limits in the following order:
First, it uses any Licensed Base remaining in the current daily or weekly cycle.
Next, it uses any Boost codes that have been added. If there are multiple codes, it will first use the one that expires soonest.
Lastly, it will use Licensed Flex.
At any point, you can see your limits by going to the Malware Details from either the options panel or the host dashboard.
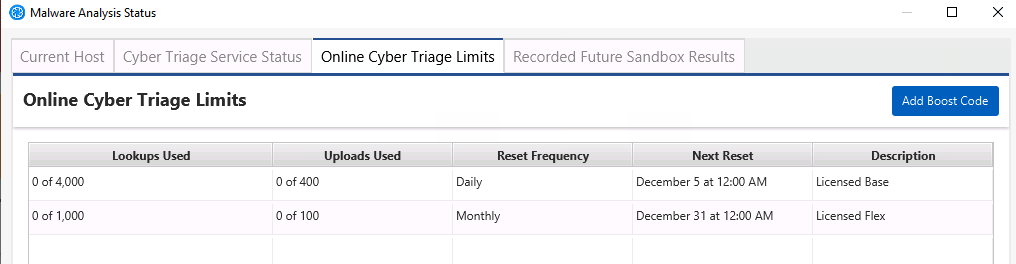
This panel will also show you how many lookups on average you use. This can help you determine when you will run out, but of course every host is different and some require more lookups than others.
8.1.5. Adding a Boost Code¶
Boost codes are valid for 30-days after they are added to Cyber Triage.
They can be used on only a single examiner system.
When added to a Team deployment, all clients will use the Boost code (analysis is done on the server)
You can purchase a Boost code via credit card at CyberTriage.com.
Once you have the code, you can enter it in several places. Cyber Triage will prompt you before and after adding a host to let you know that you are low. If you did not get a prompt, you can either get to:
The malware status from the host dashboard
Choose “View Status” from the Options panel on the Reputation Service panel.
You’ll enter a key that looks like either:
b826a555-951f-42ca-86ce-439a81106688
CT-8ed86eb5-17fc-4b3a-9b75-ce638c11b070
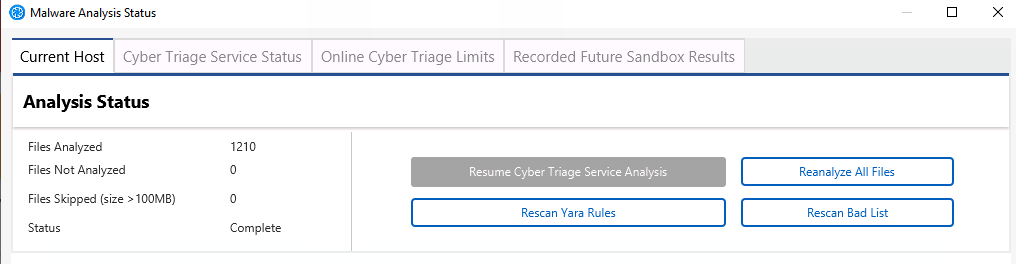
8.1.6. Resuming Malware Scanning¶
If you run out of malware lookups while analyzing a host, you have two options:
Wait until your licensed time period resets (which could be daily or weekly). You can determine this date from the Malware Details panel.
Add the Boost code as outlined above.
Once you have lookups available, you can go to the Malware Details panel and press the “Resume Analysis” button. The software should also prompt you when you re-open the host and it did not previously complete the analysis.
8.2. Yara Signatures¶
Cyber Triage can use Yara rules identify files that have patterns that have been associated with malicious activity. This allows you to import threat intelligence rules that you created or that others shared.
More details of how Yara is used can be found in Yara Rules.
8.2.1. Configure Yara Signatures¶
This section outlines where to put the rules so that they are in place when the first data is added to the system.
Cyber Triage® uses libyara 3.8.1. Documentation can be found at: https://yara.readthedocs.io/en/v3.8.1/
To include Yara signatures in the analysis, you need to copy them into a specific folder. You can find that folder by going to the Options panel.
Options Panel¶
The default path is %localappdata%\cybertriage\config\yara_rules. However, this location is can be changed by changing the data folder location in the Cyber Triage® options panel.
Cyber Triage® will not search sub directories for Yara files. If you would like to organize your Yara rules with sub directories, then you’ll need to have a Yara file in the root directory that uses an include statements to refer to the other files.
Note
You will not be able to import the entire Yara Rules GitHub repository. This repository has links between its .yar files and causes many false positives. You should copy in only the rules that you are searching for.
8.2.1.1. File Location in Team Deployment¶
When running in a Team environment, nearly all of the analysis happens on the server. The exception is memory images. Volatility is run within the client. So, if you are in a Team environment and adding memory images, you need to have the Yara rules in your local AppData folder.
8.3. Bad and Good Lists¶
Cyber Triage can use lists of indicators to identify a file as good or bad. You can import lists from threat intelligence feeds and manually add items during your analysis.
8.3.1. Configure Bad and Good Lists¶
The Options Panel has tabs for both Good and Bad Lists. From there, you can add and remove entries.
8.3.1.1. Manually Adding a List Entry From Options¶
From within the appropriate Good or Bad List panel, you can choose Add Entry to manually enter the relevant details. You will have the option of adding the item at a global level so that it applies to all future hosts or at the Incident level so that it is applied only to future hosts in the same Incident.
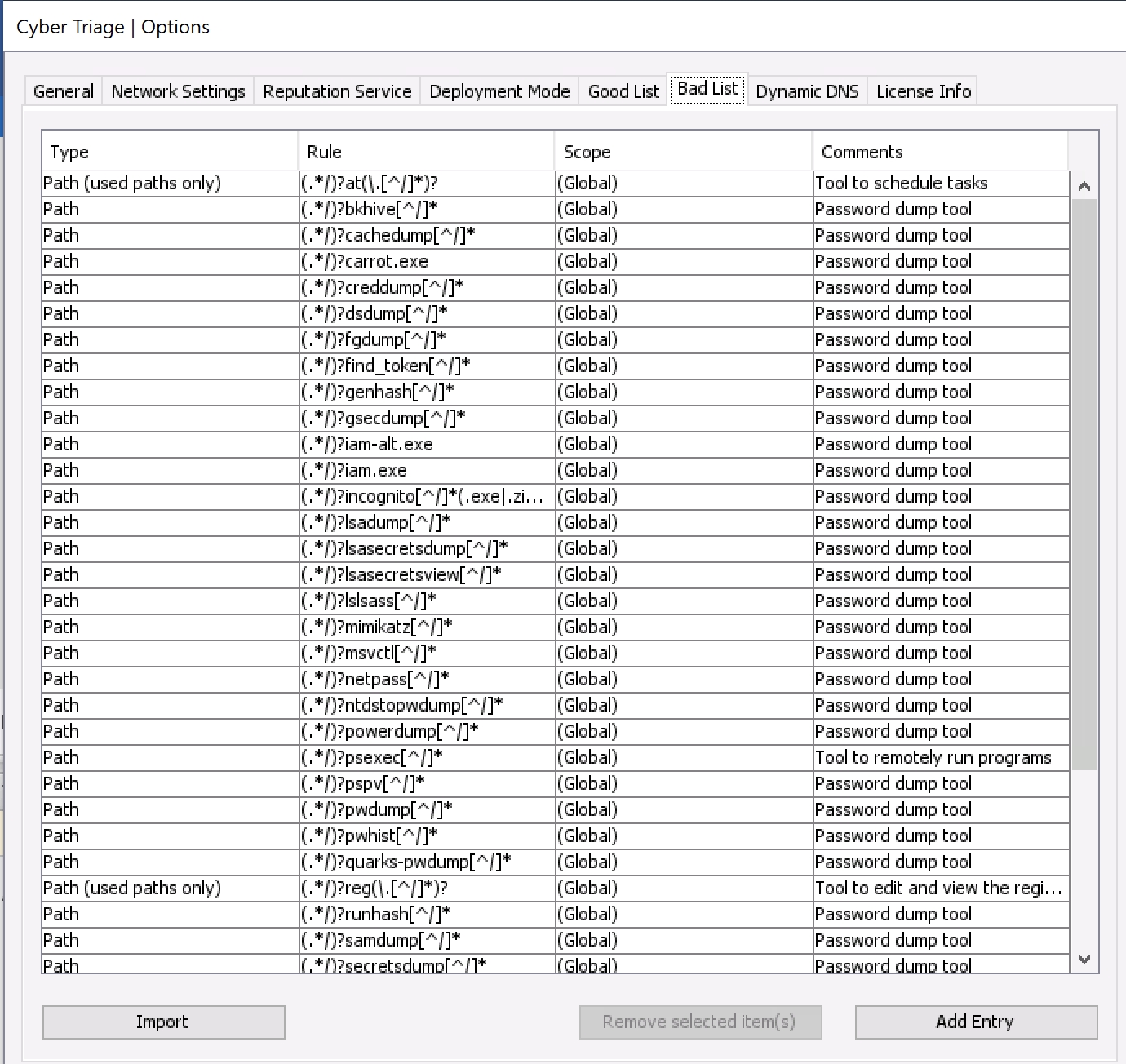
Options (Bad List Tab)¶
8.3.1.2. Importing Bad and Good Lists¶
You can bulk add Bad List items by pressing the Import button. Supported formats include:
Bad / Good List CSV format
Openphish (for Bad List items)
Cyber Triage Bad Items JSON (that was generated as a report from another Cyber Triage host).
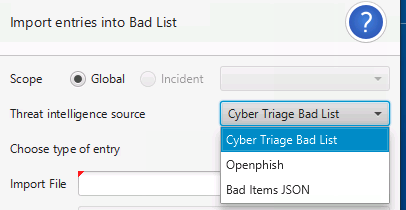
Import Bad List¶
Use the Generate Sample File button to generate a sample CSV file to determine what columns need to exist.
8.3.1.3. Removing Entries¶
One or more Good or Bad List entries can be removed from their respective tables by highlighting the entry and selecting Remove selected item(s).
8.3.1.4. Editing Lists From The Main UI¶
When analyzing host data, such as viewing all triggered tasks, you can add or remove the items from Good or Bad Lists. These options are available from right clicking.
To add an item to the Good List, right click on it and choose Add To Good List. You can then choose to add it to a global- or incident-level Good List or only for that session.
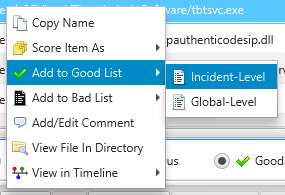
Add Item to Good List¶
Similarly, you can remove Good List entries by right clicking and choosing Remove from Good List.
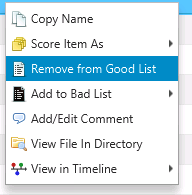
Remove Item from Good List¶