1.1. Basic Workflow¶
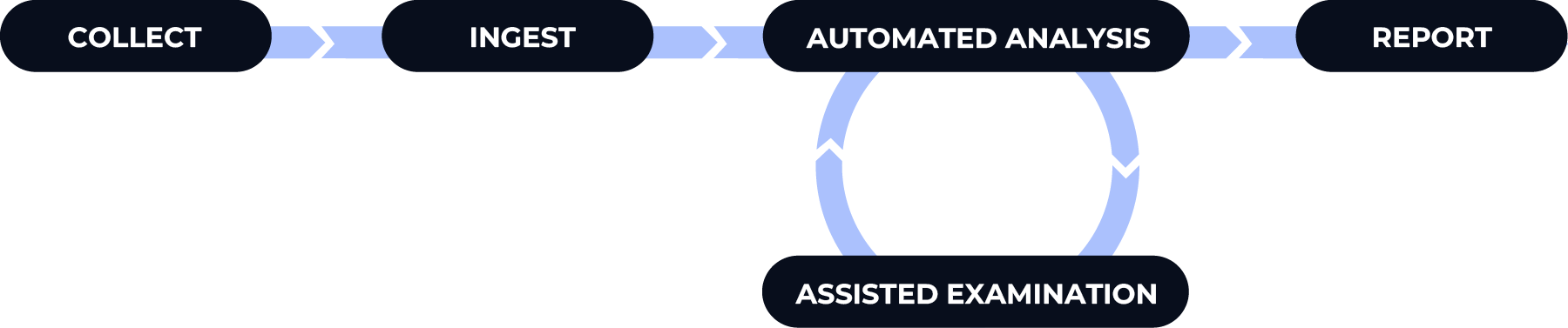
There are five basic stages to an investigation when using Cyber Triage:
Collect: Copy data from an endpoint for analysis. You can use the Cyber Triage Collector, another 3rd party collector, a full disk image, or a continous monitoring solution such as an EDR. There are a lot of ways of doing this and they are covered later on in The Cyber Triage Collector Tool.
Ingest: Import the collected data into Cyber Triage. It will normalize the data into Information Artifacts and store it in its database for analysis (see Information Artifact Types). This will be covered later on in Creating an Incident and Adding a Host.
Automated Analysis: The artifacts are sent down analysis pipelines to be scored as Bad, Suspicious, or Good. This is covered in Automated Analysis.
Assisted Examination: You can then review the findings, understand the scope, and find more evidence. This is covered in Host-level Examination.
Report: Generate human and machine readable reports with the findings. This is covered in Generating Reports.