6.3. Application Information¶
This section contains design information that could be useful as part of running and auditing the application.
6.3.1. Network Traffic (Ports and Hosts Used)¶
Some environments limit network traffic and therefore it is important to know how Cyber Triage communicates on a network to allow its traffic.
6.3.1.1. Listening Network Ports¶
The behavior of the Cyber Triage application is different depending on if it’s Standard, Team Server, or Team Client.
6.3.1.2. Standard: Listening Network Ports¶
The Standard versions of the Cyber Triage application will open occasionally open network ports when collecting data from remote systems using the Network - PsExec or Network - Manual methods. Other methods of adding data do not require listening network ports.
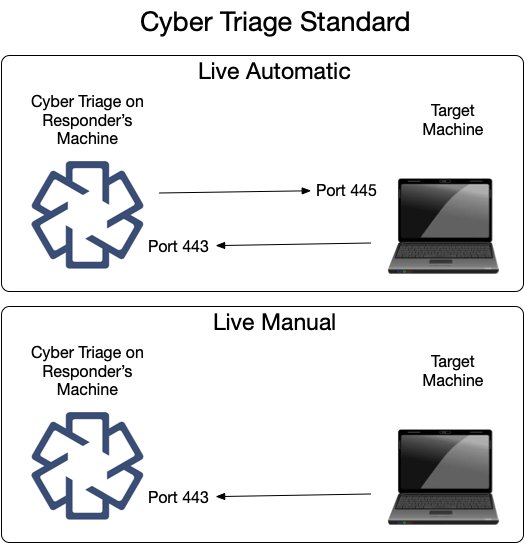
The same data is shown here in table form.
Ports Opened on Cyber Triage Machine | ||
|---|---|---|
Protocol | Port(s) | Usage (Inbound from) |
TCP | 443 | The Collector connects to Cyber Triage on this port. |
You can change this port in the Options panel. See Changing Port Number.
6.3.1.3. Team Server: Listening Network Ports¶
The Team server opens several ports for communication with clients and target systems. Not all ports are always listening. Port 443, by default, is configured to open only when certain types of collections are happening.
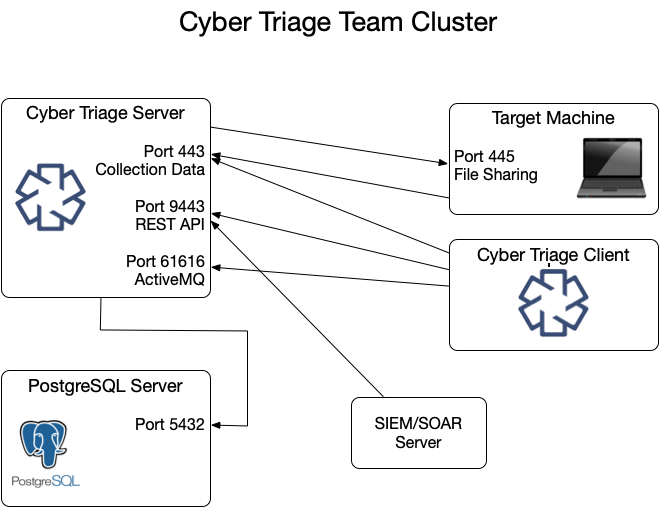
These ports are represented in various tables below.
Listening Ports on Cyber Triage Server | ||
|---|---|---|
Protocol | Port(s) | Usage (Inbound from) |
TCP | 443 | The Collector and clients connect to the server over this port to upload data. |
TCP | 9443 | REST API clients use this to retrieve data and initiate collections. |
TCP | 61616 | ActiveMQ service that keeps clients updated by sending messages. |
You can change the 443 port in the Options panel. See Changing Port Number.
It is possible, but not typical, to change the REST API and Active MQ ports.
Open up %appdata%\cybertriage\config\config.yml on the Cyber Triage® Server machine
Edit the port number for restApiPort or activeMQPort and save the file
Follow the same process to update the port on each of the Cyber Triage® client machines.
6.3.1.4. Team Client: Listening Network Ports¶
A Team Client will not have any listening ports. It will make connections only to the Team Server.
6.3.1.5. PostgreSQL Server: Listening Network Ports¶
The Cyber Triage Server will need to communicate with the PostgreSQL installation. If you installed PostgreSQL on a system other than the server, then you’ll need to make sure they can communicate.
Default PostgreSQL Port | ||
|---|---|---|
Protocol | Port(s) | Usage (Inbound from) |
TCP | 5432 | Default port PostgreSQL server listens on |
6.3.1.6. Network - PsExec Target: Listening Ports (Standard and Team)¶
To use Network - PsExec collection (Add Over The Network - PsExec Launch), Windows endpoints must have file sharing enabled so that the Collector can be copied over. This data is sent from the Cyber Triage application to the target system on the following port:
Ports Required on Target Machine for Network - PsExec | ||
|---|---|---|
Protocol | Port(s) | Usage (Inbound from) |
TCP | 445 | PsExec uses file sharing to copy and launch the Collector. |
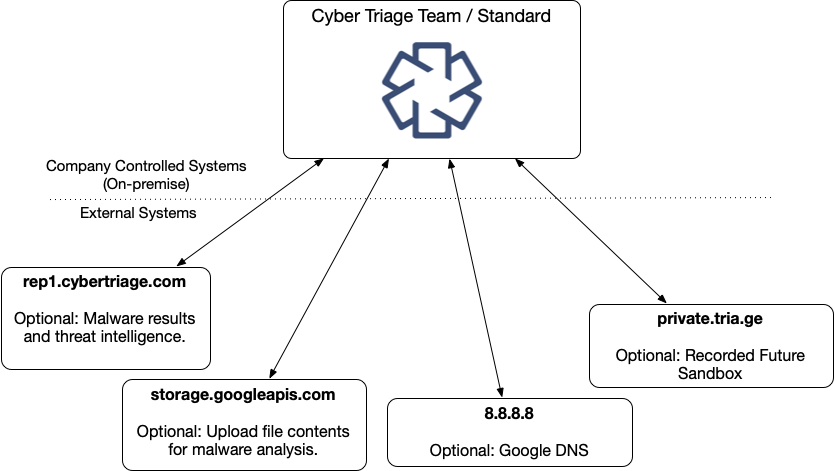
6.3.1.7. External Hosts (Standard and Team)¶
Cyber Triage will reach out to some hosts to test network settings or upload file hashes and content. If you have a proxy, you may need to add exceptions for these hosts:
External Hosts Used by Cyber Triage | ||
|---|---|---|
Host Address | Port | Usage |
rep1.cybertriage.com | 443 | Used to query for malware analysis results and threat intelligence. |
storage.googleapis.com | 443 | Used to upload file content for malware scanning. |
8.8.8.8 | 443 | Google DNS - Used to resolve host names and detect dynamic DNS. |
private.tria.ge | 443 | Used to upload files to the Recorded Future Sandbox. |
6.3.2. Security Features¶
6.3.2.1. Access Control¶
The following principles are used to limit access to the data stored in the application:
The Standard versions will only have open network ports when the user is adding a host. Otherwise, it should not be able to receive data from external hosts. Access is granated only by the user having interactive access to the host running Cyber Triage.
The Team versions have APIs that are listening for connections, but will first authenticate the user based on the Cyber Triage username and password.
Any user with access to the computer running Cyber Triage may have access to stored data based on their OS-level permissions.
6.3.2.2. Encryption¶
The following encryption is used in the application:
- Data in Transit:
Network traffic between the Server and Clients and between the Collector and the Server is encrypted with TLS 1.2. See below for information on verifying the certificates.
PostgreSQL: Traffic between the Server and PostgreSQL can be encrypted with TLS.
- Data at Rest: The following file-based encryption is used:
Output of Collector: The user can choose to encrypt the output with a 4096-bit RSA public key and 256-bit AES ECB symmetric encryption.
Secrets: Sensitive data is stored encrypted in Java Keystore.
Passwords: User passwords are stored as bcrypt hashes.
Once the data is on the Cyber Triage server, it is not stored encrypted within the database or local files. File system-level encryption should be used if all of your data at rest must be encrypted.
6.3.2.3. TLS Certificates¶
Cyber Triage uses TLS to encrypt various network communications:
Between the Collector and Cyber Triage
Between the Team Server and Clients
Between the ActiveMQ Server and Clients
In most environments, there is nothing to configure. You just need to know about the certificate that was generated for you. But, you may need to configure Cyber Triage to know about a TLS intercept proxy, if you have one.
6.3.2.3.1. Certificate Verification¶
To prevent man in the middle attacks:
Cyber Triage generates a unique self-signed certificate for each application installation.
Cyber Triage applications connecting to the server will verify the hash value of the certificate they receive.
The Collector will be passed in the server’s certificate hash as a command line argument. If the certificate it receives in the TLS handshake is different, the connection will be dropped.
The Team Client will be prompt the user to confirm the server certificate hash the first time it connects. Once that value is locally saved, the Client will use it to verify each connection. If the Client receives a new certificate during the handshake, it will prompt the user.
6.3.2.3.2. Internal Intercept Proxies¶
If your network has a proxy that decodes TLS traffic, then you need to add configure Cyber Triage to know about it. When configured, Cyber Triage will use the proxy certificate to validate the connection with clients and the Collector.
From the Options Panel, you can import the certificate used by the Proxy in the “System” / “Certificate Info” section.
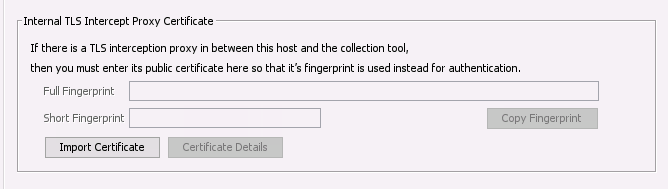
Add TLS Intercept Proxy Certificate¶
6.3.2.4. Logging¶
Logs are stored in the ‘var\log’ folder in the data directory (see Data Folder).
For a Team Server:
All API requests are logged
Default retention is 20 days
You need to choose and configure a log collector to send them to a central location. Examples.